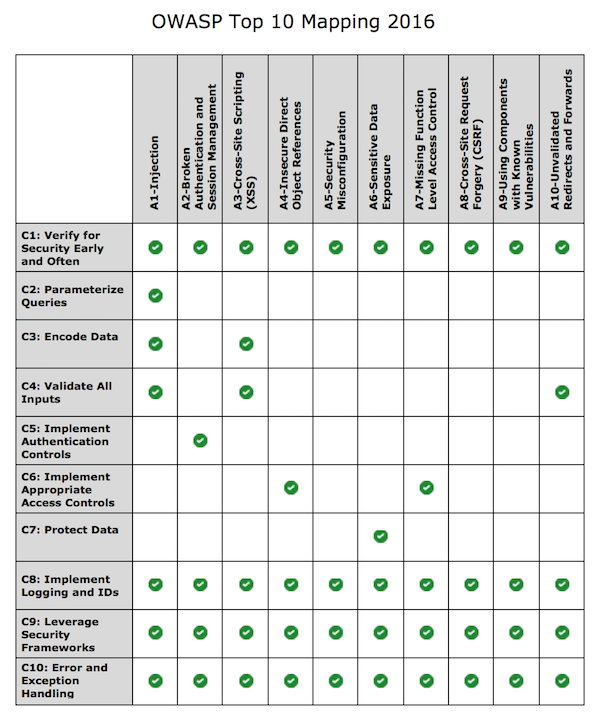
PDF) AN ASSIGNMENT ON OWASP top 10 Security threat and map with top 10 proactive controls to mitigate the risk of web application

OWASP Top 10: Injection Attacks. Understanding Injection… | by Jeremiah Talamantes | Dec, 2023 | Compliiant.io Blog
www-project-proactive-controls/v3/en/c8-protect-data-everywhere.md at master · OWASP/www-project-proactive-controls · GitHub
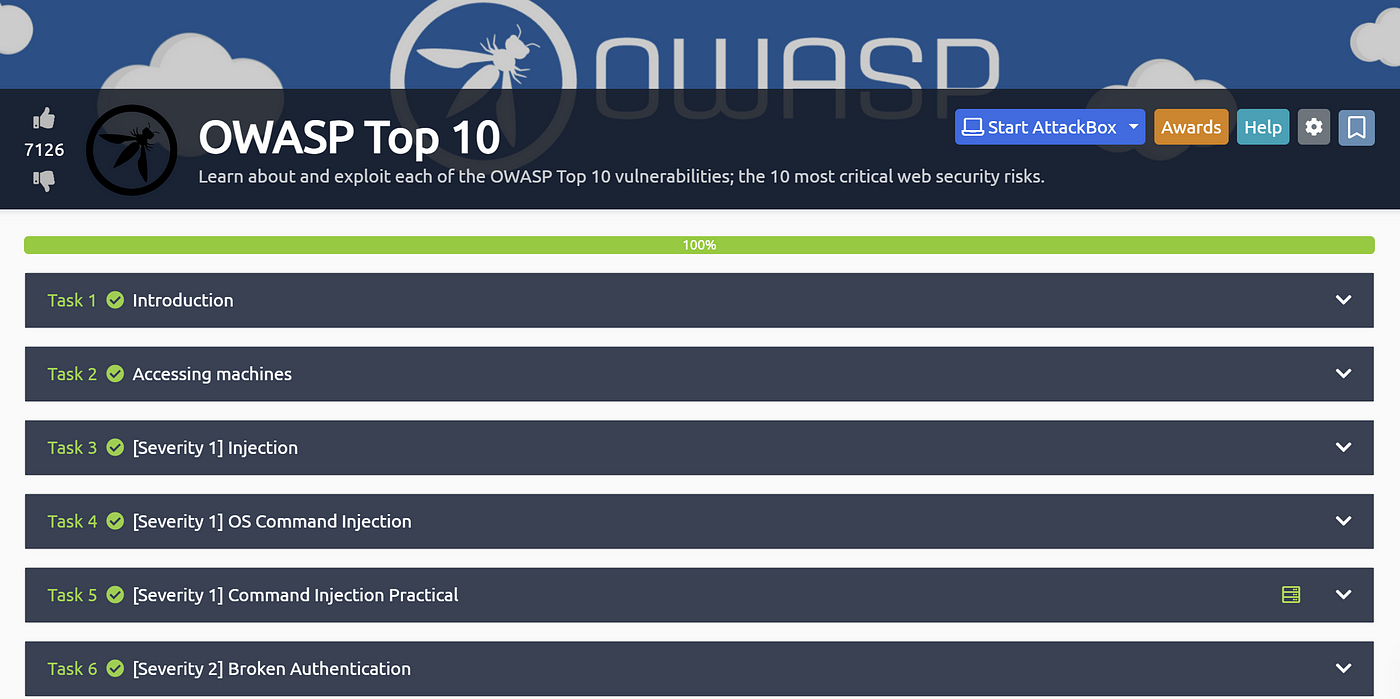
OWASP Top 10 | TryHackMe Writeup. This document delves into the OWASP Top… | by Lixin Zhang | Medium