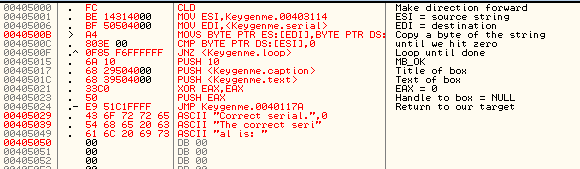
![Backdoor 101] Backdooring PE File w/ User Interaction & Custom Encoder Using Existing Code Cave - Hack.Learn.Share Backdoor 101] Backdooring PE File w/ User Interaction & Custom Encoder Using Existing Code Cave - Hack.Learn.Share](https://captmeelo.com/static/img/2018-07-21-backdoor101-part2/28.png)
Backdoor 101] Backdooring PE File w/ User Interaction & Custom Encoder Using Existing Code Cave - Hack.Learn.Share

An example of incoherence between the main memory and the instruction... | Download Scientific Diagram
![Backdoor 101] Backdooring PE File w/ User Interaction & Custom Encoder Using Existing Code Cave - Hack.Learn.Share Backdoor 101] Backdooring PE File w/ User Interaction & Custom Encoder Using Existing Code Cave - Hack.Learn.Share](https://captmeelo.com/static/img/2018-07-21-backdoor101-part2/16.png)
Backdoor 101] Backdooring PE File w/ User Interaction & Custom Encoder Using Existing Code Cave - Hack.Learn.Share






/codecave2.png)
/demo3.png)

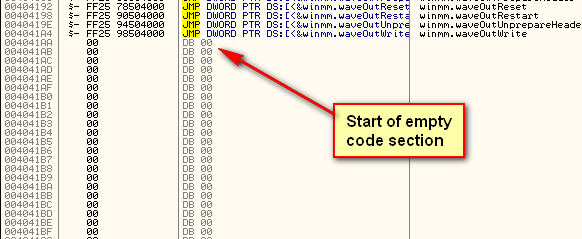

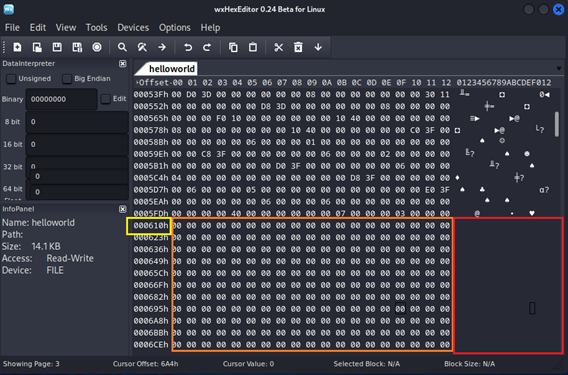
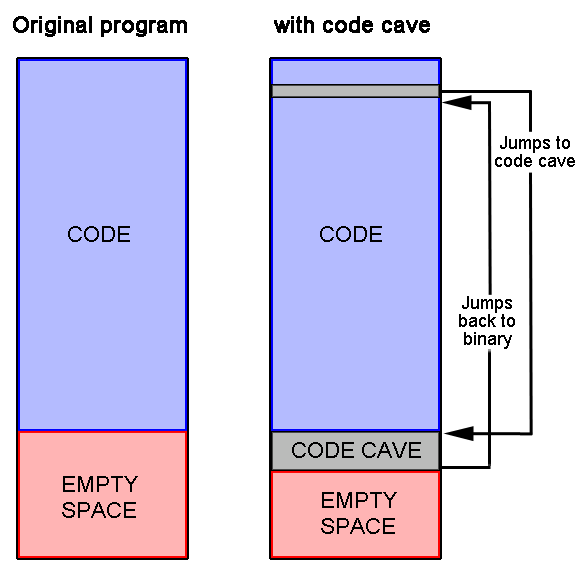
![ExpDev] Weaponizing Your Favorite PE — Portable Executable Exploit | by bigb0ss | InfoSec Write-ups ExpDev] Weaponizing Your Favorite PE — Portable Executable Exploit | by bigb0ss | InfoSec Write-ups](https://miro.medium.com/v2/resize:fit:1400/1*EgmyIFTV5y7Zq3I6J_lC0Q.png)
![ExpDev] Weaponizing Your Favorite PE — Portable Executable Exploit | by bigb0ss | InfoSec Write-ups ExpDev] Weaponizing Your Favorite PE — Portable Executable Exploit | by bigb0ss | InfoSec Write-ups](https://miro.medium.com/v2/resize:fit:1124/1*4Wzz4_8L6PS__oKsegy8dg.png)