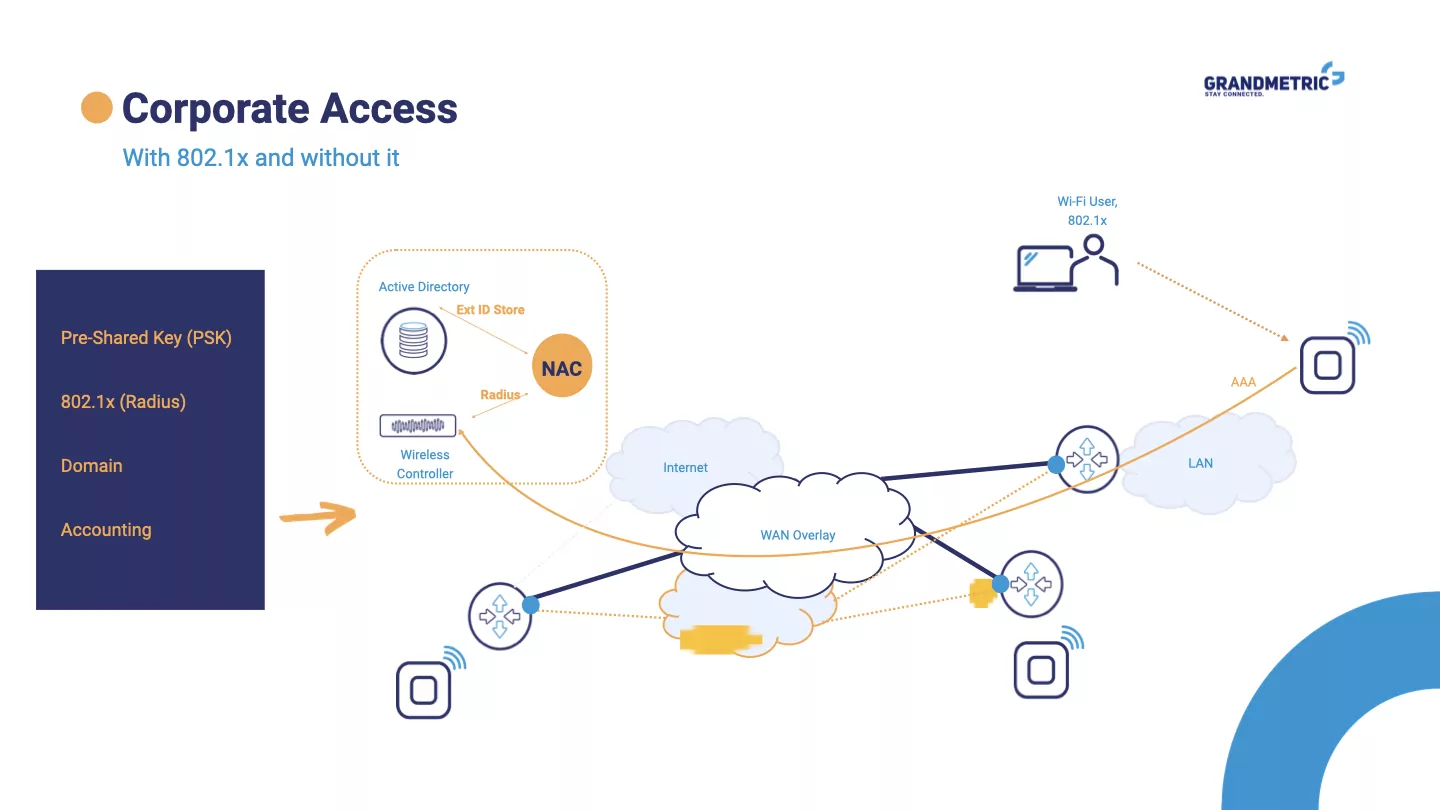
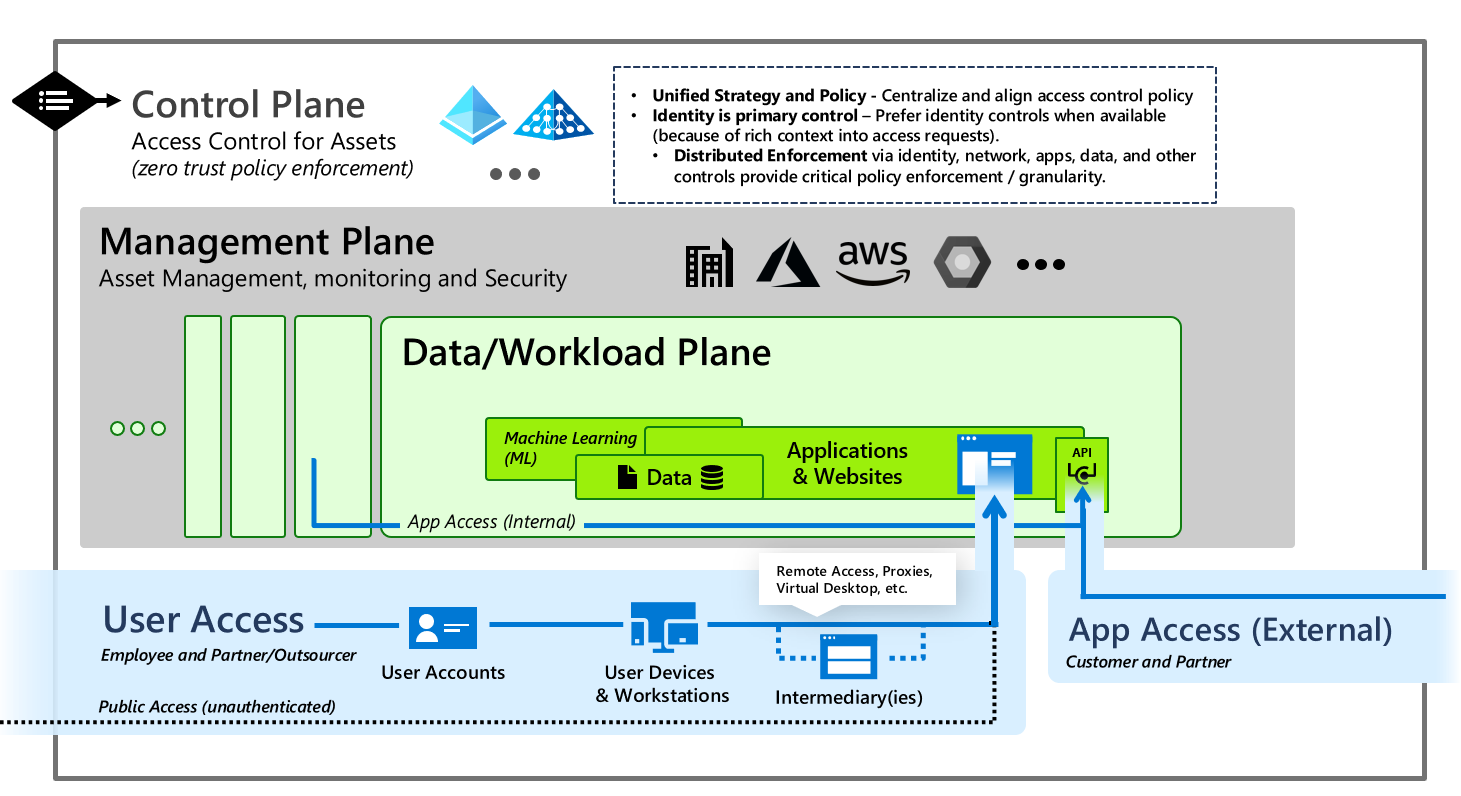
Figure 2 from Network access control (NAC): An open source analysis of architectures and requirements | Semantic Scholar
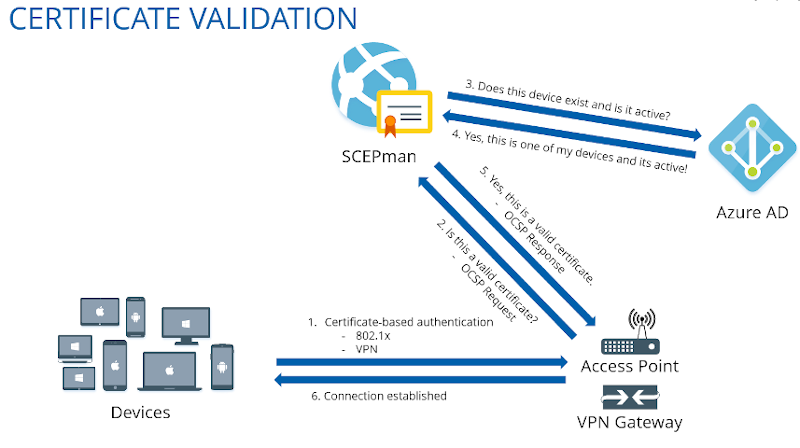
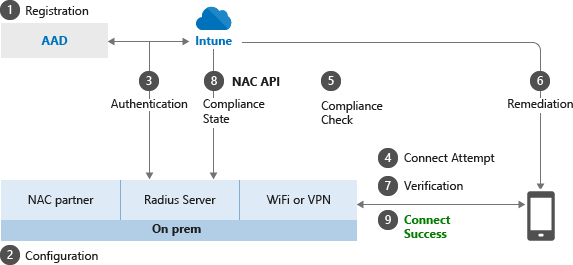
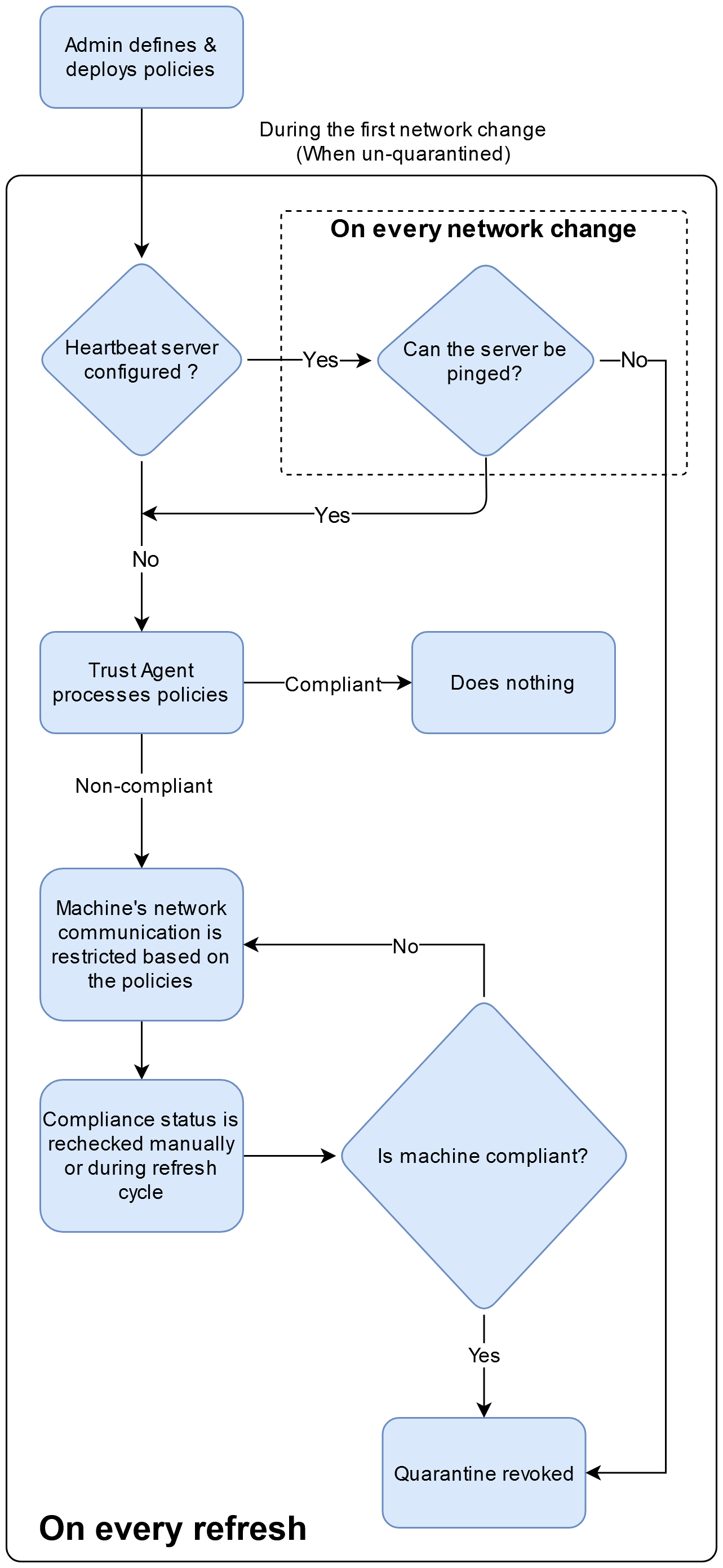
Cloud-Native, Modern Solution to 802.1x Network Access Control on Azure AD devices - Part One — Joe's Tech Space

FIX: Computer cannot be connected. You must Enable COM+ Network Access in Windows Firewall. - WinTips.org

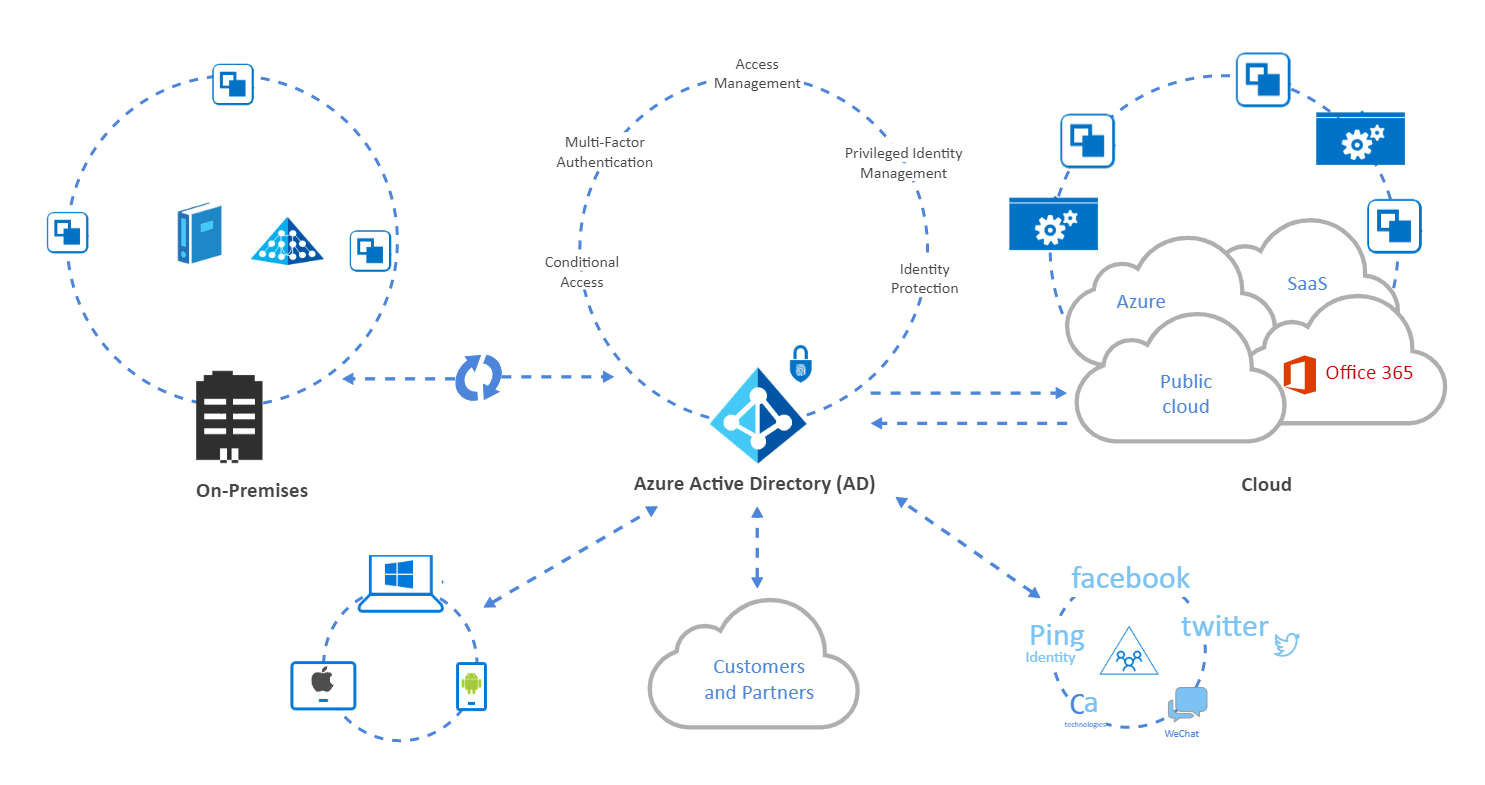
Use attribute-based access control with AD FS to simplify IAM permissions management | AWS Security Blog

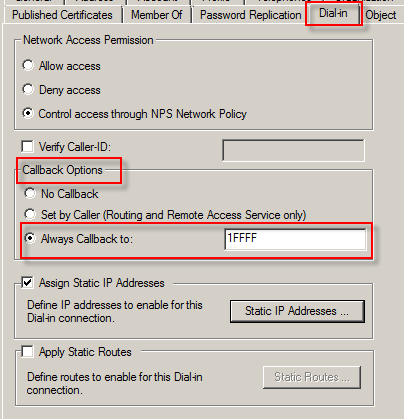
Secure Wireless Access and Authentication with Radius on WS2012R2 Network Policy Server . | Chinny Chukwudozie, Cloud Solutions.