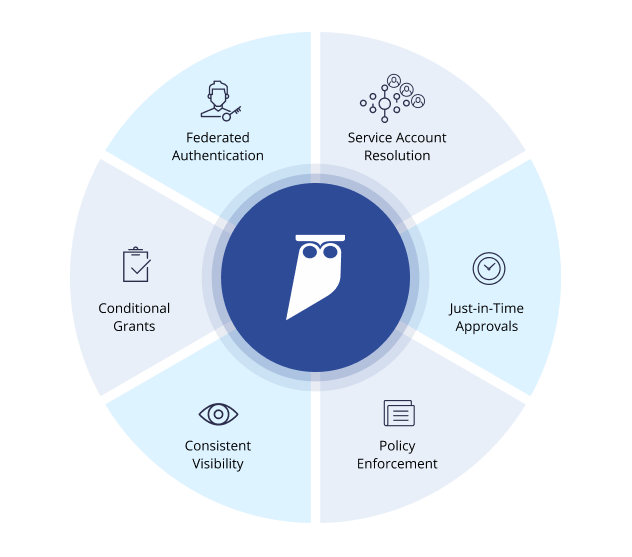
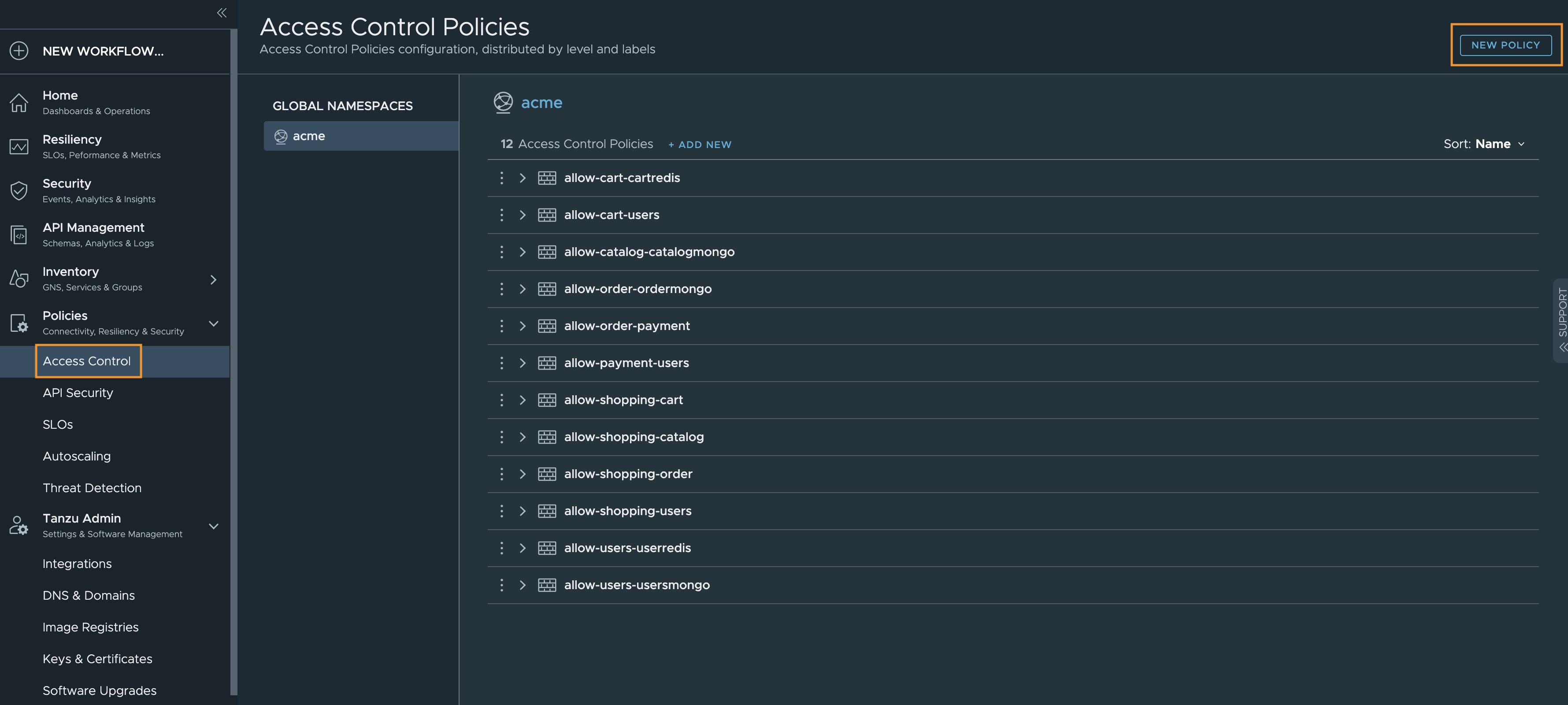
Policy-based access control in application development with Amazon Verified Permissions | AWS DevOps Blog
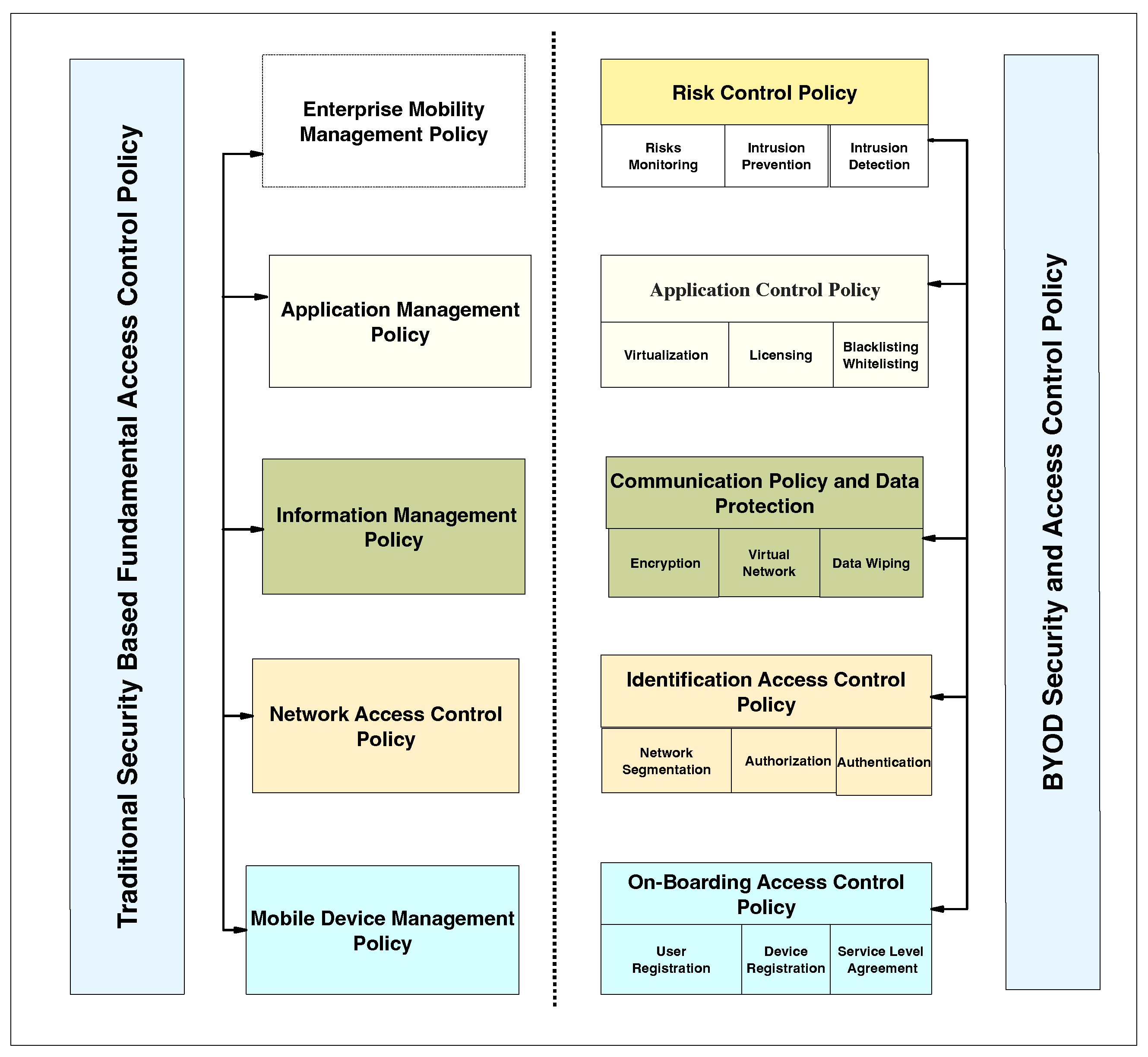
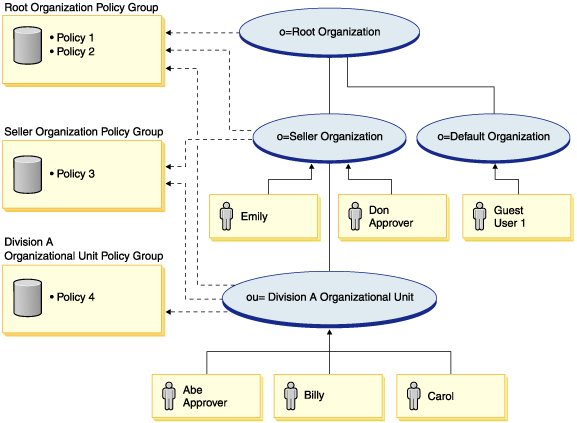
Applied Sciences | Free Full-Text | Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions


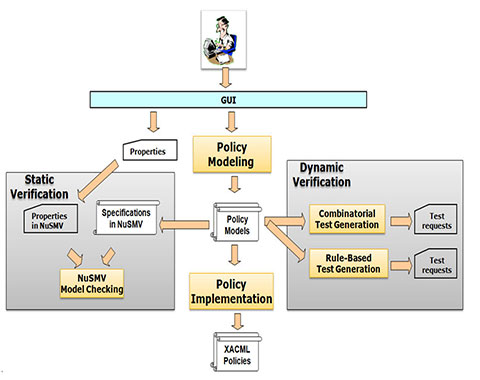
![ISO 27001 Access Control Policy Ultimate Guide [plus template] ISO 27001 Access Control Policy Ultimate Guide [plus template]](https://hightable.io/wp-content/uploads/2021/04/ISO27001-Access-Control-Policy-Template-Example-1-722x1024.png)




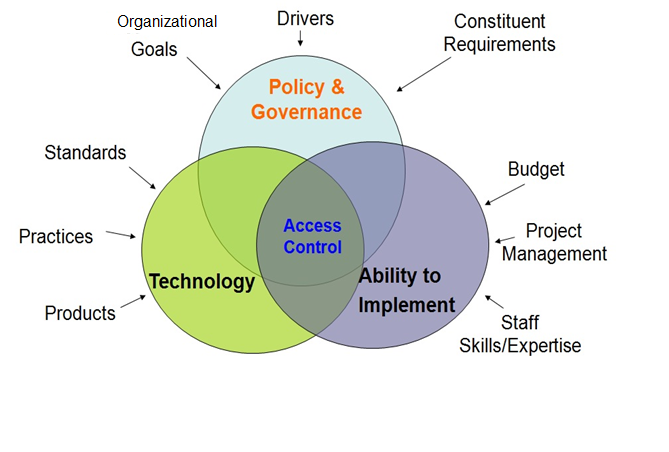
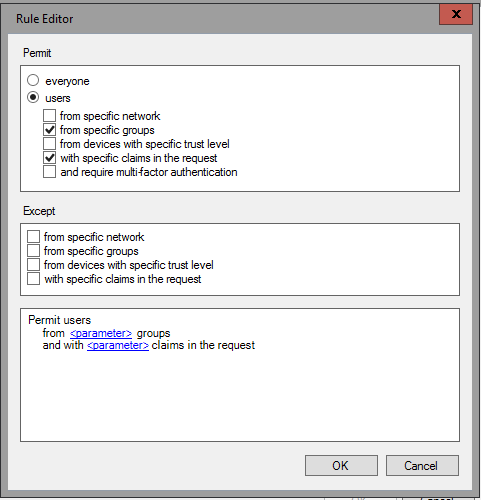


![PDF] Database Access Control Policies | Semantic Scholar PDF] Database Access Control Policies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bfd4c8c86b964e3843b853d311181a12267c5633/3-Figure3-1.png)