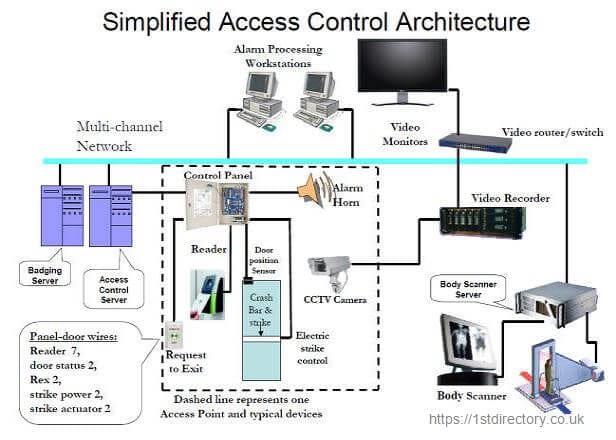
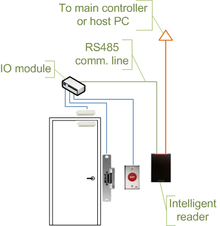
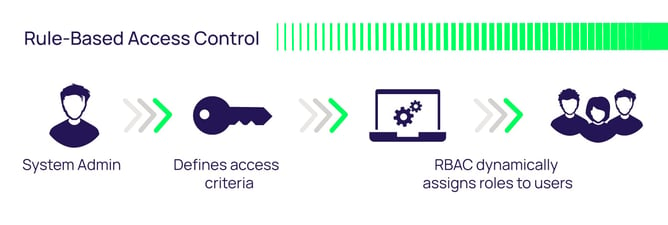
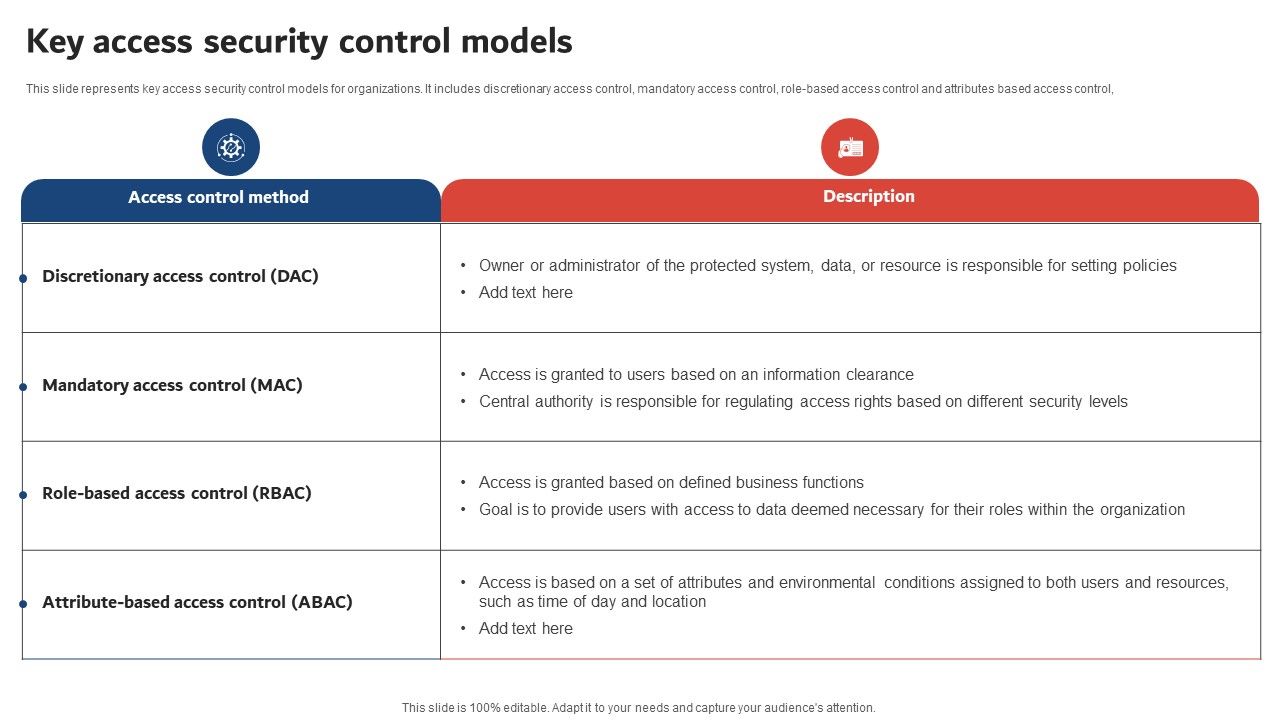
A capability-based security approach to manage access control in the Internet of Things - ScienceDirect

Rationale for the RBAC96 family of access control models | Proceedings of the first ACM Workshop on Role-based access control

PDF) Comparative Study on Access Control Models for Privacy Preservation | Nasriah Zakaria - Academia.edu


![PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4dd58d7ef7f99a18255704c0733da18c49154787/4-Table1-1.png)

![PDF] Hybrid Access Control Model in Semantic Web | Semantic Scholar PDF] Hybrid Access Control Model in Semantic Web | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e266034e425943fd92f6fa1444e1f0fb5f58c63f/2-Figure1-1.png)



![PDF] A Lattice-Based Privacy Aware Access Control Model | Semantic Scholar PDF] A Lattice-Based Privacy Aware Access Control Model | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/526f8193583c8461f2181ab139fc3c0133f98abe/4-Figure2-1.png)