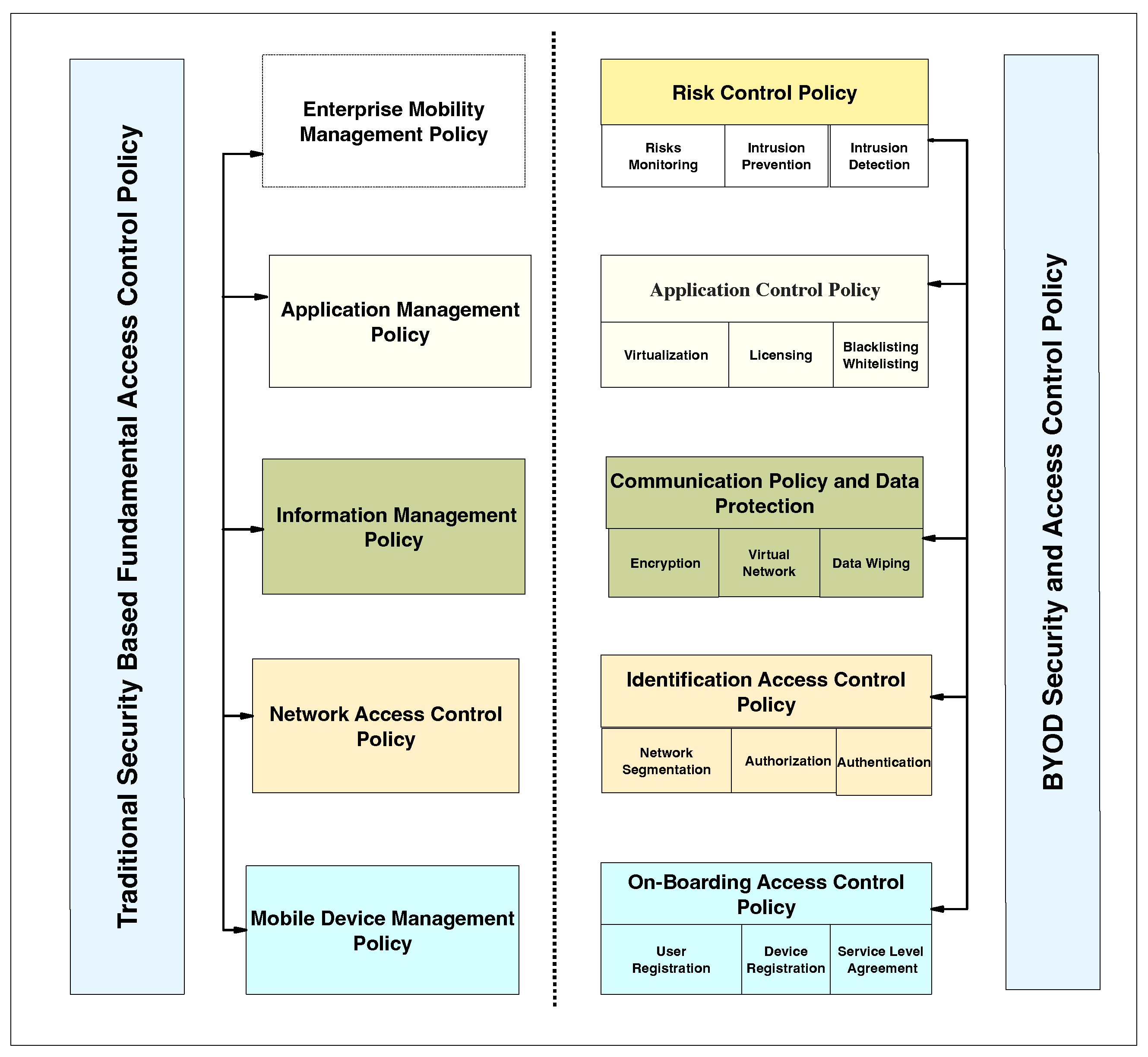
A Guide to Claims-Based Identity and Access Control: Authentication and Authorization for Services and the Web: Authentication and Authorization for Services, Web, and the Cloud : Baier, Dominick, Bertocci, Vittorio, Brown, Keith,

A Guide to Claims-Based Identity and Access Control: Authentication and Authorization for Services and the Web : Baier, Dominick, Bertocci, Vittorio, Brown, Keith, Densmore, Scott, Pace, Eugenio, Woloski, Matias: Amazon.it: Libri

Authentication and Access Control - Boonkrong, Sirapat - Ebook in inglese - EPUB3 con Adobe DRM | IBS

Access Control. To start off with the topic first we'll… | by Nisal Sudila | Technology Hits | Medium