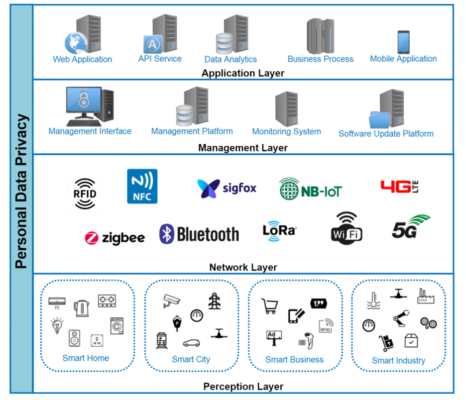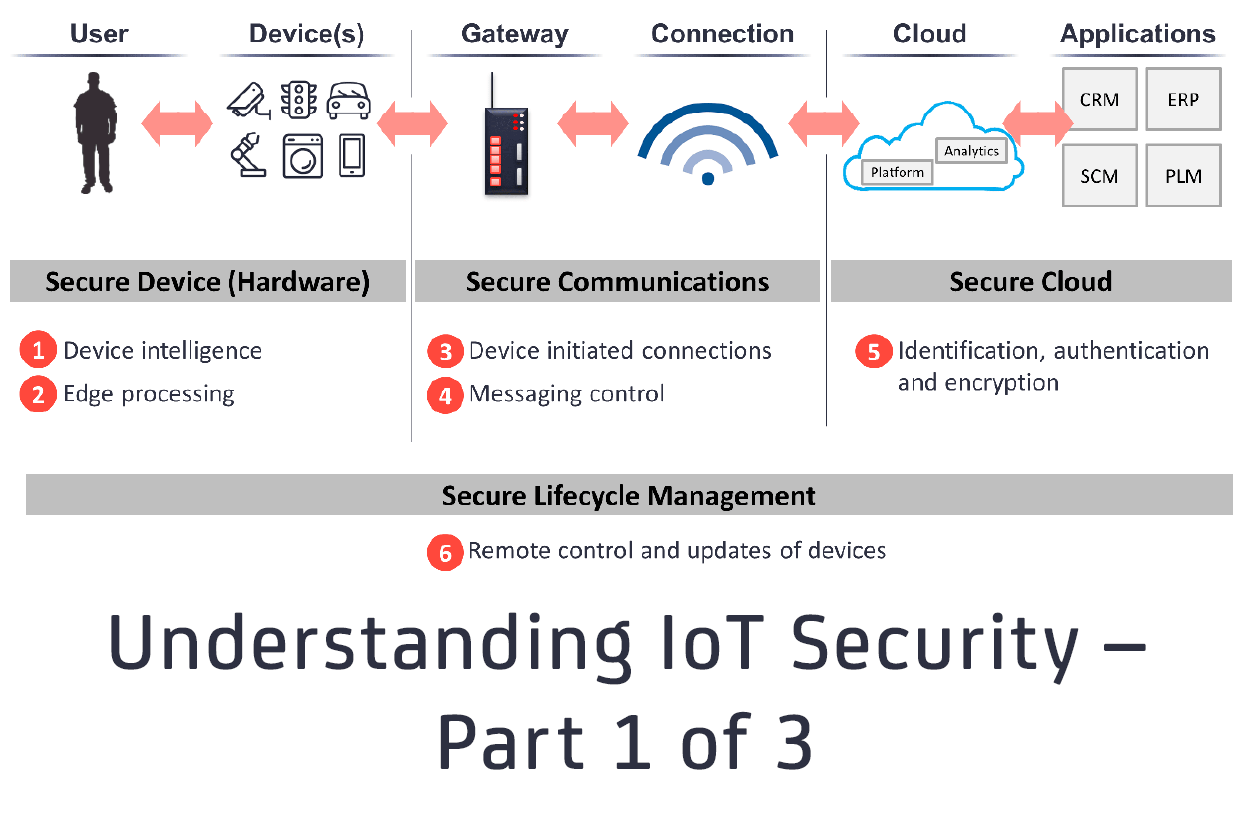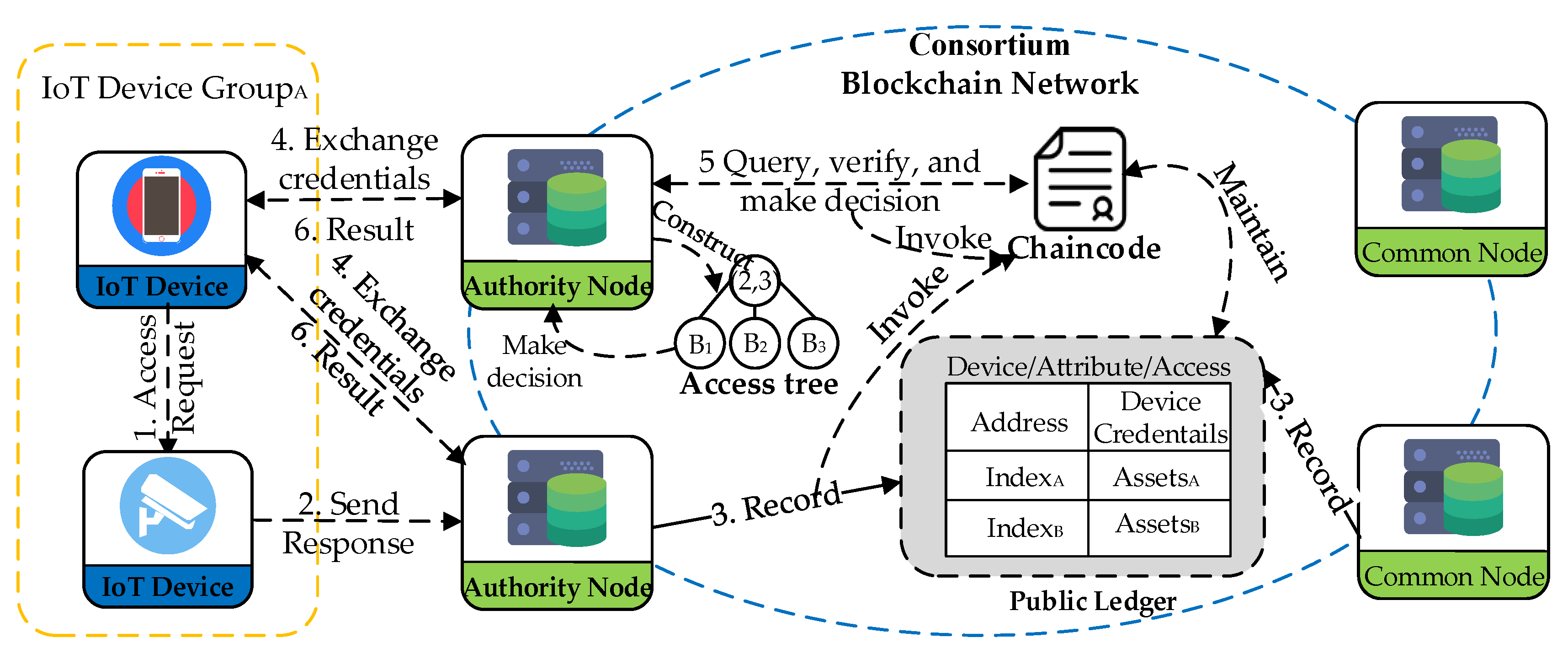
Electronics | Free Full-Text | An Attribute-Based Collaborative Access Control Scheme Using Blockchain for IoT Devices
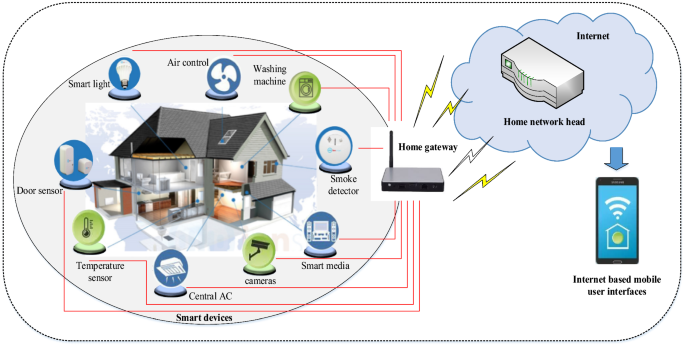
Secure user authentication and key agreement scheme for IoT device access control based smart home communications | Wireless Networks

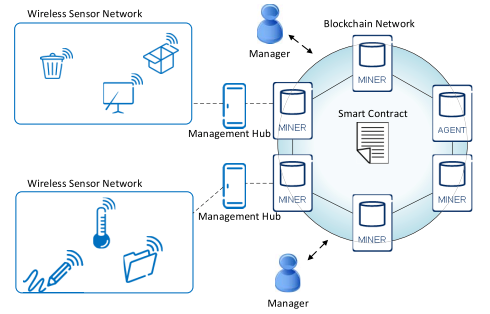
Distributed access control solution for the IoT based on multi-endorsed attributes and smart contracts | Semantic Scholar
Your must-have IoT security checklist: ENISA's online tool for IoT and Smart Infrastructures Security — ENISA
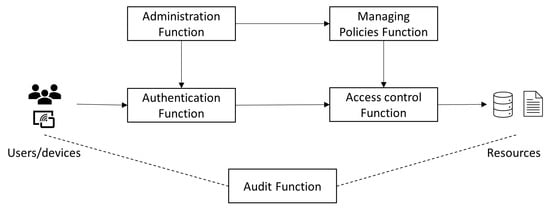
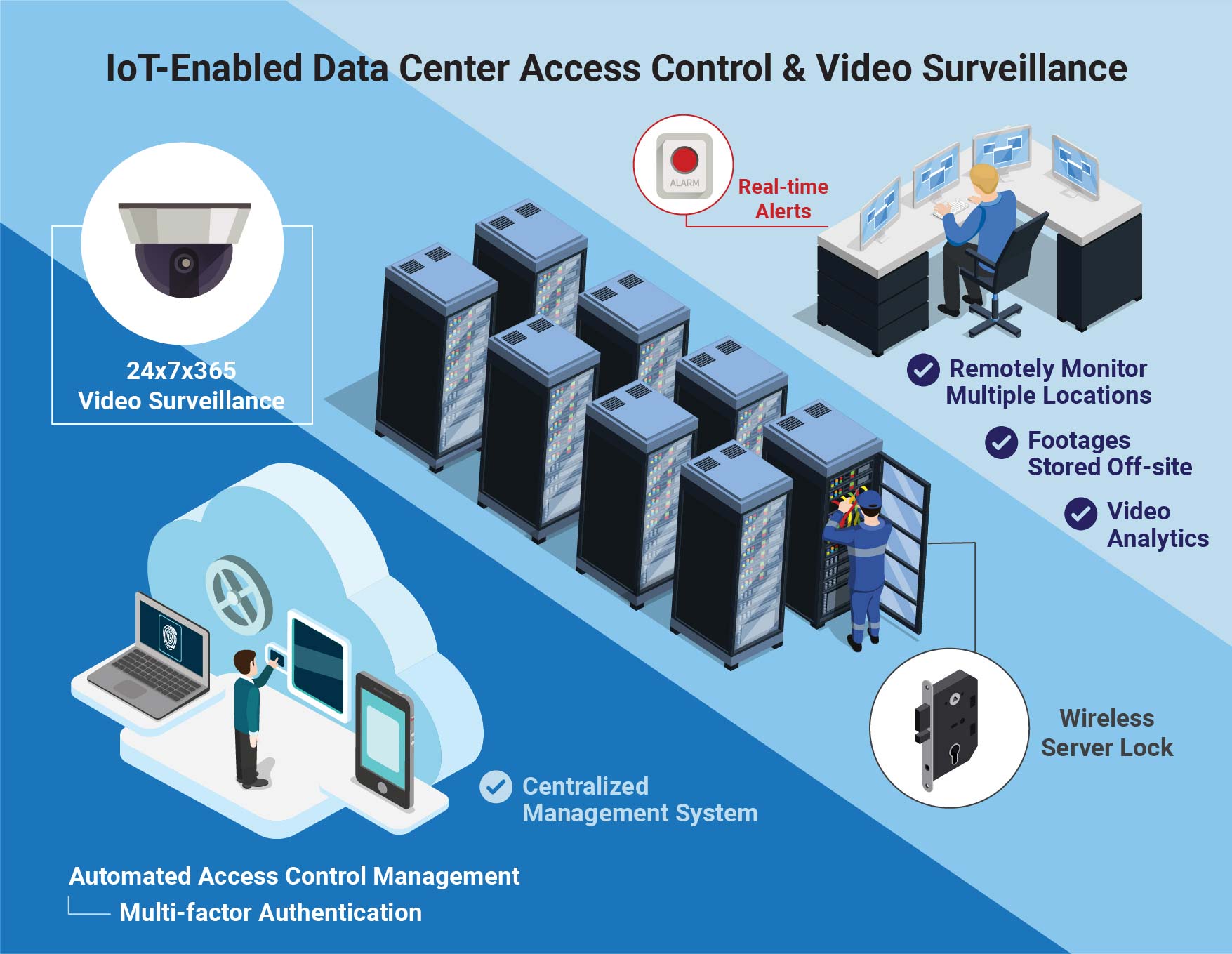
Sensors | Free Full-Text | Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions